Network diagram

Configure inside and outside interface
ciscoasa(config)# int gi0/1 ciscoasa(config-if)# nameif outside INFO: Security level for "outside" set to 0 by default. ciscoasa(config-if)# ip address dhcp setroute ciscoasa(config-if)# no shut ciscoasa(config-if)# int gi0/0 ciscoasa(config-if)# nameif inside INFO: Security level for "inside" set to 100 by default. ciscoasa(config-if)# ip address 172.18.1.1 255.255.255.224 ciscoasa(config-if)# no shut
Self signed certificate
ciscoasa(config)# hostname vpn
vpn(config)# domain-name cyruslab.net
vpn(config)# clock timezone SGT 8
vpn(config)# ntp server 118.189.177.157 prefer
vpn(config)# sh ntp associations
address ref clock st when poll reach delay offset disp
~118.189.177.157 118.189.138.5 2 3 64 0 8.5 35742. 16000.
* master (synced), # master (unsynced), + selected, - candidate, ~ configured
vpn(config)#
vpn(config)# crypto key generate rsa label rsa-key modulus 2048 noconfirm
INFO: The name for the keys will be: rsa-key
Keypair generation process begin. Please wait...
vpn(config)# crypto ca trustpoint self
vpn(config-ca-trustpoint)# keypair rsa-key
vpn(config-ca-trustpoint)# fqdn vpn.cyruslab.net
vpn(config-ca-trustpoint)# subject-name CN=vpn.cyruslab.net
vpn(config-ca-trustpoint)# enrollment self
vpn(config-ca-trustpoint)# exit
vpn(config)# crypto ca enroll self
% The fully-qualified domain name in the certificate will be: vpn.cyruslab.net
% Include the device serial number in the subject name? [yes/no]: yes
Generate Self-Signed Certificate? [yes/no]: yes
vpn(config)#
Trustpoint is the container for certificate. The enrollment self command means self-signed certificate.
Enable the self-signed trustpoint
The self-signed certificate will be enabled on the interface where the VPN will terminate, in this lab is outside interface
vpn(config)# ssl trust-point self outside
Export the certificate to the vpn user computer
vpn(config)# crypto ca export self identity-certificate The PEM encoded identity certificate follows: -----BEGIN CERTIFICATE----- MIIDHDCCAgSgAwIBAgIEScjJVzANBgkqhkiG9w0BAQUFADBQMRkwFwYDVQQDExB2 cG4uY3lydXNsYWIubmV0MTMwEgYDVQQFEws5QVdORDlHVUVHTDAdBgkqhkiG9w0B CQIWEHZwbi5jeXJ1c2xhYi5uZXQwHhcNMTYwOTAyMTkxMjQ5WhcNMjYwODMxMTkx MjQ5WjBQMRkwFwYDVQQDExB2cG4uY3lydXNsYWIubmV0MTMwEgYDVQQFEws5QVdO RDlHVUVHTDAdBgkqhkiG9w0BCQIWEHZwbi5jeXJ1c2xhYi5uZXQwggEiMA0GCSqG SIb3DQEBAQUAA4IBDwAwggEKAoIBAQCZO/HICWkfpBeVEEd7n7PYICFYmC8ngyAB xKsmic5tt95Rs7K36wiC+V3t01eO375L7EORtAkiZwo3sHFggZpb4LrSBVQI7Wb1 E/uRMX/8GKkZoPrwYIu7P1oLCBVI7Jh/XUyhNP9S01EfalfQQ7syZmk+O2M6GlQ8 FukffEv8g6PclavZYcbH8CytrtJAGD7J4Sv3BgJMu4z1y/cqf1v11xb7keLHlaD1 r4gpmJNstFEyn9YDU/O644FiikibsBnBNGAw8E2vNLBZSzMXzkZz+NlW1OLnods0 emQ7UOtnoRi6R4c1nmIMYpjtaiNWAnM254beUHZi4cJfjacFVq1DAgMBAAEwDQYJ KoZIhvcNAQEFBQADggEBAIp7JGh6n95IQd47vypn0C3FBexlasuWmQuyFEeZFXLr iYClsdvqirJJFWMIKPOxTk67tSGG6yom7D6OiJSOtZLtGk0ee5zhY6PFxqRldzXp +sCzYN0WYjV04r8U3j8NYnwGwc9kDw2Iz0VQydds1JOblXbh83iQaeLmA+lGTDk0 6tmqbeXzUquPwNslEp0ibZ+Lw/tvllIg+k5BmdYD9zoZyas/AlN+c7ady6qol1jt 3GllGap6B+NL4o0YQBmSAv63/obTUGObevnQxK1EmAoxUnE1nITzJdsEgSswYLhy WlkKubqXwzojhb7M2cSLJTDOV/9clayrJB2chnCKXKg= -----END CERTIFICATE----- vpn(config)#
Copy and paste from BEGIN CERTIFICATE until END CERTIFICATE and save as cert.cer. If you are using Windows you can use certmgr.msc and import the certificate. See screenshot below.

On Linux:
cyrus@cyrus-vm:~$ sudo nano /usr/local/share/ca-certificates/cert.cer
Then copy the certificate:
SSL VPN begins….
vpn(config)# username cyrus password P@ssw0rd vpn(config)# username cyrus attributes vpn(config-username)# service-type remote-access
This account solely for remote access vpn only.
vpn(config)# ip local pool VPN 192.168.100.1-192.168.100.14 mask 255.255.255.240
Allocate a pool for vpn user after successfully login.
vpn(config)# webvpn vpn(config-webvpn)#anyconnect image disk0:/anyconnect-linux-64-4.0.00048-k9.pkg vpn(config-webvpn)# anyconnect enable vpn(config-webvpn)# enable outside INFO: WebVPN and DTLS are enabled on 'outside'. vpn(config-webvpn)# tunnel-group-list enable
anyconnect enable to enable anyconnect and enable outside and enable webvpn on the outside interface. tunnel-group-list enable to enable drop down box on the anyconnect vpn client for group selection.
vpn(config)# group-policy VPN internal
Internal means the group-policy is stored locally.
vpn(config)# group-policy VPN attributes vpn(config-group-policy)# address-pools value VPN vpn(config-group-policy)# dns-server value 8.8.8.8 8.8.4.4 vpn(config-group-policy)# gateway-fqdn value vpn.cyruslab.net vpn(config-group-policy)# vpn-tunnel-protocol ssl-client ssl-clientless vpn(config)#access-list SPLIT-TUNNEL standard permit 172.18.1.0 255.255.255.224 vpn(config)# group-policy VPN attributes vpn(config-group-policy)# split-tunnel-policy tunnelspecified vpn(config-group-policy)# split-tunnel-network-list value SPLIT-TUNNEL vpn(config-group-policy)# split-tunnel-all-dns disable vpn(config-group-policy)# split-dns value cyruslab.net vpn(config-group-policy)# default-domain value cyruslab.net vpn(config-group-policy)# vpn-idle-timeout 60 vpn(config-group-policy)# vpn-simultaneous-logins 1
This group-policy defines which VPN address assignment after successfully login, and also perform split tunnel.
Any traffic that matches SPLIT-TUNNEL is tunneled through the vpn.
Only DNS query for *.cyruslab.net will be tunneled through else the rest of the dns queries will not be tunneled.
The vpn idle timeout is set to 1 hour and only one login at any time no concurrent login is allowed.
To specify for ssl anyconnect client connection or webvpn (browser based) clientless connection methods.
vpn(config)# tunnel-group VPN type remote-access vpn(config)# tunnel-group VPN general-attributes vpn(config-tunnel-general)# default-group-policy VPN
Only need to define the default group policy, the rest leave as default. Anything default will be inherited from this “invisible” default group-policy DfltGrpPolicy, you can only see this group-policy when you issue show run all group-policy. This default group-policy cannot be deleted.
vpn(config-tunnel-general)# tunnel-group VPN webvpn-attributes vpn(config-tunnel-webvpn)# group-alias VPN
Only create a group which will be displayed as a drop down box in Anyconnect client. The rest will be default settings inherited from “invisible” default tunnel group known as DefaultWEBVPNGroup similar to DfltGrpPolicy this cannot be deleted and can only be shown by using show run all tunnel-group
vpn(config)# vpn-sessiondb max-anyconnect-premium-or-essentials-limit 2
Ok this is stupid in my opinion, this command should not even exist!
If you do not specify there will be no connection available! If you buy license for example like 300 make sure you use this command and make the number to 300! Otherwise you will have users complaining cannot connect! This command simply means allowing 2 concurrent anyconnect vpn.
vpn(config)# sysopt connection permit-vpn
This command tells ASA to close a blind-eye whenever vpn traffic enters. Yeah it simply bypass whatever rules you set…
vpn(config)# http redirect outside 80
Ok simply to redirect http request to https… make your vpn user easier when they use the clientless.
Let’s test it!

Ok the redirection works, i used http instead of https…

On linux is a bit problematic on installing Cisco anyconnect client, so I use openconnect instead
apt install network-manager-openconnect
It is command line….:
cyrus@cyrus-vm:~/Downloads/binaries$ sudo openconnect vpn.cyruslab.net POST https://vpn.cyruslab.net/ Attempting to connect to server 172.16.10.18:443 SSL negotiation with vpn.cyruslab.net Server certificate verify failed: signer not found Certificate from VPN server "vpn.cyruslab.net" failed verification. Reason: signer not found Enter 'yes' to accept, 'no' to abort; anything else to view: yes Connected to HTTPS on vpn.cyruslab.net Got HTTP response: HTTP/1.0 302 Object Moved GET https://vpn.cyruslab.net/ Attempting to connect to server 172.16.10.18:443 SSL negotiation with vpn.cyruslab.net Server certificate verify failed: signer not found Connected to HTTPS on vpn.cyruslab.net Got HTTP response: HTTP/1.0 302 Object Moved GET https://vpn.cyruslab.net/+webvpn+/index.html SSL negotiation with vpn.cyruslab.net Server certificate verify failed: signer not found Connected to HTTPS on vpn.cyruslab.net Please enter your username and password. GROUP: [VPN]:VPN Please enter your username and password. Username:cyrus Password: POST https://vpn.cyruslab.net/+webvpn+/index.html Got CONNECT response: HTTP/1.1 200 OK CSTP connected. DPD 30, Keepalive 20 Connected tun0 as 192.168.100.1, using SSL Established DTLS connection (using GnuTLS). Ciphersuite (DTLS0.9)-(RSA)-(AES-256-CBC)-(SHA1).
Ok a new virtual interface appears known as tun0

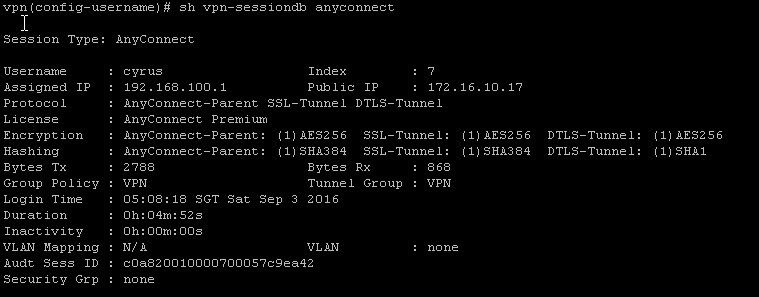
Ok so from my Cisco ASA gateway I can see this connection: